FlexiHub Team uses cookies to personalize your experience on our website. By continuing to use this site, you agree to our cookie policy. Click here to learn more.
Since the advent of the Internet, Internet users have always faced one challenge or the other. One of such problems is the fact that it's hard for users to trust any code that is published on the Internet. Users can't do without downloading software from the Internet to their computers regularly. Some software can contain threats or malicious programs that put the information and the security of users at risk.
The developers can nullify this threat by digitally signing every software before making them available for download by Internet users. When software is signed, it's easier for users to verify its origin, as well as verify that it has not been altered or tampered with in any way.

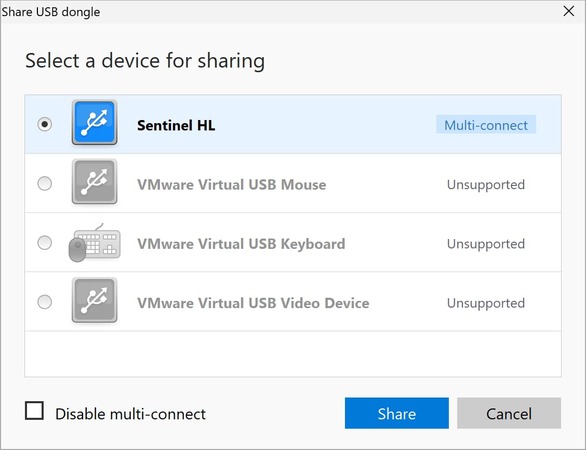
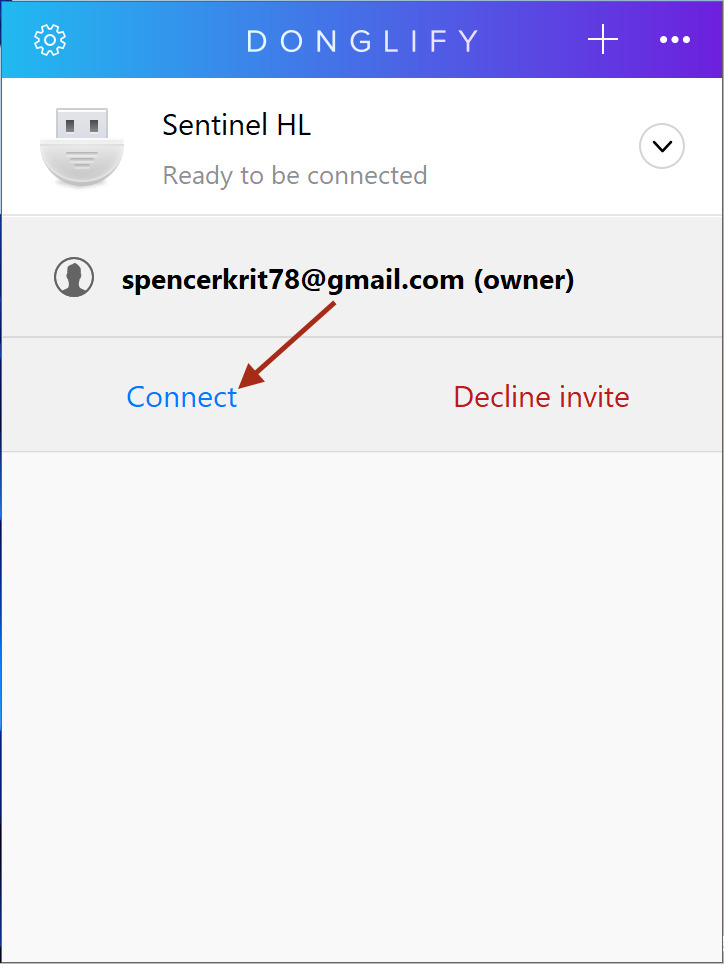
Yes, it’s that easy! This way, you won’t have to purchase any extra hardware solutions or use any questionable software, whenever you need to share a digital certificate token.
The best way to share a USB token for macos/windows is with the heil of Donglify. That way, everyone in the office can make use of the dsc dongle, and it will always remain in the same place.
At Donglify, we know that when it comes to working with digital certificates and license dongles, security isn’t optional - it’s essential. Whether you’re connecting from your home office or halfway around the world, you can count on your data being protected every step of the way.
With all these safeguards in place, you can be confident that your USB dongles, certificates, and sensitive data remain secure, wherever and whenever you need to access them.
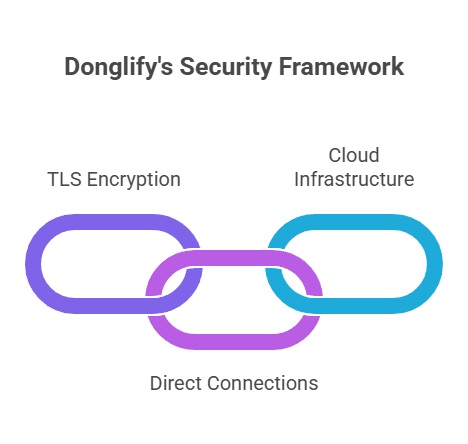
Strong Protection
Every bit of information you transfer is wrapped in TLS 1.2 encryption, the same standard trusted by banks and leading tech companies. That means your data travels through a safe, private tunnel that outsiders simply can’t break into.
End-to-End Safety
Whenever possible, Donglify creates a direct, point-to-point connection between devices. This minimizes the number of stops your data has to make. And even if it does pass through our servers, it stays encrypted and anonymous the whole way.
Reliable Cloud Infrastructure
Behind the scenes, Donglify runs on Akamai’s global cloud network—one of the most trusted names in internet security. This ensures your connections are fast, resilient, and can bounce back quickly if there’s ever a hiccup.
Code signing simply refers to the signing of scripts using a certificate-based digital signature. The aim is to verify the identity of authors and to make sure that the code has not been altered since the author signed it following Microsoft’s digital certification standards. That way, other software, and users can determine whether they can trust the software.
With a Microsoft code signing certificate, it's possible for you to sign code while making use of a private and public key (a similar method to the one used by SSH and SSL). When the certificate is requested, a public/private key pair is generated. This private key remains on the machine of the applicant and never gets sent to the certificate provider. When the public key is requested by the provider, it is sent, and then the provider will issue a certificate.
The types of code signing that are accepted to be most advanced are known as "extended validation code signing certificates." The reason they are rated so highly is that they deal with two of the most common loopholes exploited by the developers of malware to propagate their malicious code - poor private key protection and weak identity verification processes.
The former is achieved through the adoption of two-factor authentication – the private key is encrypted on the token and stored on a USB dongle. It will be impossible for those who don't have the physical device to sign code using your code signing certificate.
Although the USB key offers the best protection possible, it may still not be very convenient to use it in the company, as there's a chance that the dongle will be passed among members and can get lost in the process. Also, we recommend that you do not copy, clone, duplicate USB dongle as it's not a practice that falls on the right side of the manufacturers’ ToS.